Hierarchy Takeover via NTLM Coercion and Relay to MSSQL
Introduction
This post is part of a series on SCCM exploitation. If you haven’t yet, don’t miss SCCM Range Deployment — it’s like setting up your own SCCM sandbox, minus the sand in your underwear.
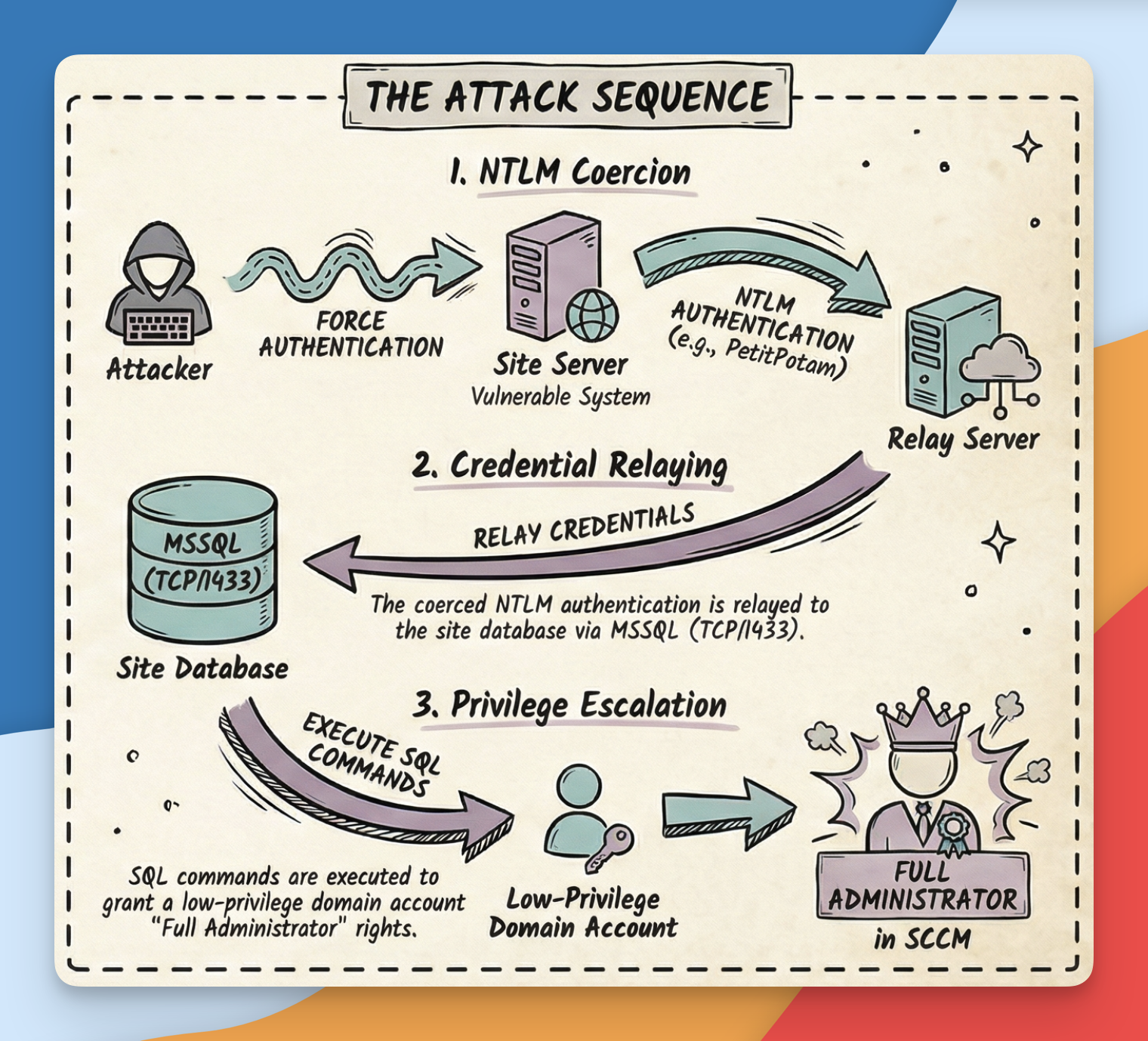
At the end of this post, you will know how to coerce a SCCM Primary Site Server into authenticating against you, and relay that authentication back to the Server Site Database. What for you might ask? To make an arbitrary domain account a member of the SMS Admins group, which, granted the right permissions at the database level, will give you remote command execution as SYSTEM on the entire SCCM fleet.